Table of Contents
This article is the third and last post of the trilogy about Open edX Security. As an Open edX developer, I will summarize everything you should know about security vulnerabilities.
To understand the importance, it is better first to define that vulnerability; for that, I will use a quote.
“A vulnerability is a hole or a weakness in the application, which can be a design flaw or an implementation bug, that allows an attacker to cause harm to the stakeholders of an application.” OWASP Foundation
Understanding common vulnerabilities and exploitation techniques allows us to write more secure code and identify and fix potential weaknesses before they become serious problems.
On the other hand, 45% of the mail Open edX receives about security and vulnerabilities comes from managers. This reason makes our participation as Open edX developers important.
Ready, now, how can I contribute?
First, you should know that most vulnerability reports come from questions: Should this work like this? Why?
If you consider that something has a behavior that does not seem correct and could generate some vulnerability, you can
Send an email to security@openedx.org to report the anomaly.
⚠️ It is not a good idea to publish this in public channels, as it would make life easier for anyone intending to attack and hurt the platform.

What if I have no idea what kinds of things might be risky?
The Open Worldwide Application Security Project (OWASP) created a list of the top 10 vulnerabilities recognized globally by developers. Here is a table with examples to keep them in mind.
| Vulnerability | Example | Look at |
| Broken access control: | “I had permission to do this, but right now, no.” “As a non-superuser, I had access to endpoints that I shouldn’t have. ” | Permissions |
| Cryptographic failures: | “Is any data transmitted in clear text?” | HTTP vs HTTPS |
| Injection: | “The user can break the platform by adding code in the username box in the login.” | Validate, filter, and sanitize the inputs. |
| Insecure design: | “Having ways to have a certificate without passing an exam. Trying to cheat.” | Ways to don’t allow cheating flows. |
| Security misconfiguration: | “Unnecessary features are enabled or installed by default.” | Default configuration |
| Outdated components: | “If the software is vulnerable, unsupported, or out of date.” | Update requirements |
| Auth failures: | “Is it hard to cheat or auth?” | Authentication |
| Integrity failures: | “Where objects or data are encoded or serialized into a structure that an attacker can see and modify is vulnerable to insecure deserialization.” | Verify the data is from the expected and trusted source. |
| Observability failures: | “Events not logged or have unclear log messages.” “No trigger alerts for active attacks in real-time or near.” | Logs and Monitoring |
| URL forgeries: | “Can I trust my URLs?” | Sanitize and validate inputs and enforce the URL schema. |
If you want more information about these ten vulnerabilities and how to prevent them, you can review the first post of our security series or the OWASP explanations and recommendations.
And how do I know how serious a vulnerability is?
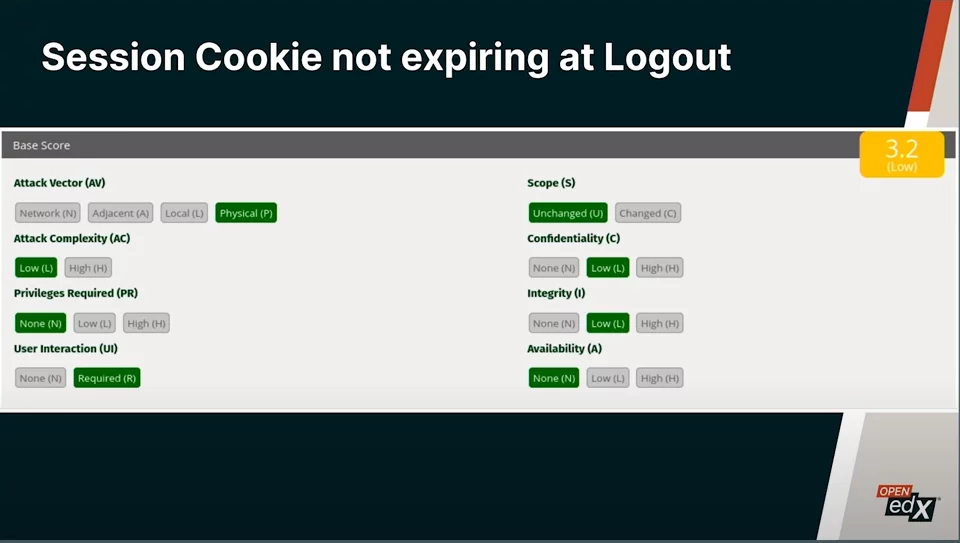
Open edX uses a tool called CVSS to score the priority of an exposure. The CVSS tool calculates the score from different sections. As with the ten vulnerabilities, we will summarize these eight axes CVSS uses to score a vulnerability.
| Vector | Questions |
| Attack Vector (AV): | Do they need access to a physical device, or can they do it from the network to exploit this vulnerability? |
| Attack Complexity (AC): | Is the attack easy to accomplish, or do you need deep knowledge about what you are doing? |
| Privileges required (PR): | Do you need privilege, or can anyone attack? |
| User interaction (UI): | Do you need someone to do something? |
| Scope (S): | When you attack, do you have access to one thing, or can you expand your access? |
| Confidentiality ©: | Are we going to have our data exposed? |
| Integrity (I): | Can someone change the information in our system? |
| Availability (A): | Can they turn down the platform? |
Conference Safer The History & Future of Open edX Security. Open edX, 2023. Available at: https://youtu.be/WRJAox_8YY0?t=1226.
In the example, it was calculated with the “Base Score” sections, which is what Open edX usually uses to rate vulnerabilities. Still, the tool gives the possibility to analyze more things.
You can check the second post of our security series or review the CVSS Specification Document directly.
About the Security Working Group
If you are passionate about security or want to get more involved in triaging Open Source Vulnerabilities, read the OEP-60 Open Source Security Working Group and contact the Security Working Group.

Final recommendations:
Applying security measures should be a proactive process, not a reactive one. Therefore, it is good to consider the top 10 vulnerabilities when developing. Still, we can start with these five measures:
- Apply Access Controls: Restrict user privileges based on roles, ensuring that only authorized actions can be performed within the system.
- Encrypt Sensitive Data: Protect user data by encrypting it at rest and in transit. Use industry-standard encryption algorithms for maximum protection.
- Validate User Input: Implement input validation mechanisms to prevent malicious data entry that can compromise system integrity.
- Update Dependencies: Regularly update third-party libraries and dependencies used in your codebase. Outdated versions may contain known vulnerabilities that hackers can exploit.
- Enforce Strong Authentication: Secure access points with strong passwords, multi-factor authentication, or Single Sign-On (SSO) options to fortify user accounts.
And if you find any vulnerability, do not panic. Write to security@openedx.org and do not publicly expose this possible vulnerability. This group will tell you the best way to address it.
Remember, securing your Open edX instance is an ongoing process. By following these guidelines, you’re taking important steps toward maintaining a safe learning environment for all users! 🚀🔒